4 minutes
TryHackMe Writeup: Net Sec Challenge
| Net Sec Challenge | Difficulty: Medium |
|---|
“Use this challenge to test your mastery of the skills you have acquired in the Network Security module. All the questions in this challenge can be solved using only
nmap,telnet, andhydra.”
The first three questions can be answered by scanning all the ports between 1 to 65535 using nmap -p- flag. Or you could slice the scans to practice more nmap flags.
What is the highest port number being open less than 10,000?
As I stated before, one way to answer this question is to scan all the ports and then find the highest open port less than 10,000. Or, as shown below, only scan the ports between 1000 and 10,000.
$ sudo nmap -sS -p1000-10000 [MACHINE_IP]
The highest open port is: 8080 .
There is an open port outside the common 1000 ports; it is above 10,000. What is it?
With -p flag, a hyphen can be used to specify greater than or equal or less than or equal a port number. For example, if a hyphen is before a number, like nmap -p -57 [MACHINE_IP], nmap will scan from port 1 to port 57. Because the end of the range was specified, but the beginning was excluded. On the other hand, if a hyphen is after a number, such as, nmap -p 57- [MACHINE_IP] the beginning of the range was specified, but the end was excluded. For this reason, nmap will start the scan from port 10000 to the last port possible, 65535.
Now, to find the open port over 10,000, the starting port of the scan will be specified -10,000- but the end port will be excluded, so nmap will scan from port 10,000 to port 65535:
$ sudo nmap -sS -p 10000- [MACHINE_IP]
Or, scan all the port and exclude ports between 1 to 10,000:
$ sudo nmap -sS -p- --exclude-port 1-10000 [MACHINE_IP]
Answer: 10021
How many TCP ports are open?
6 ports are open.
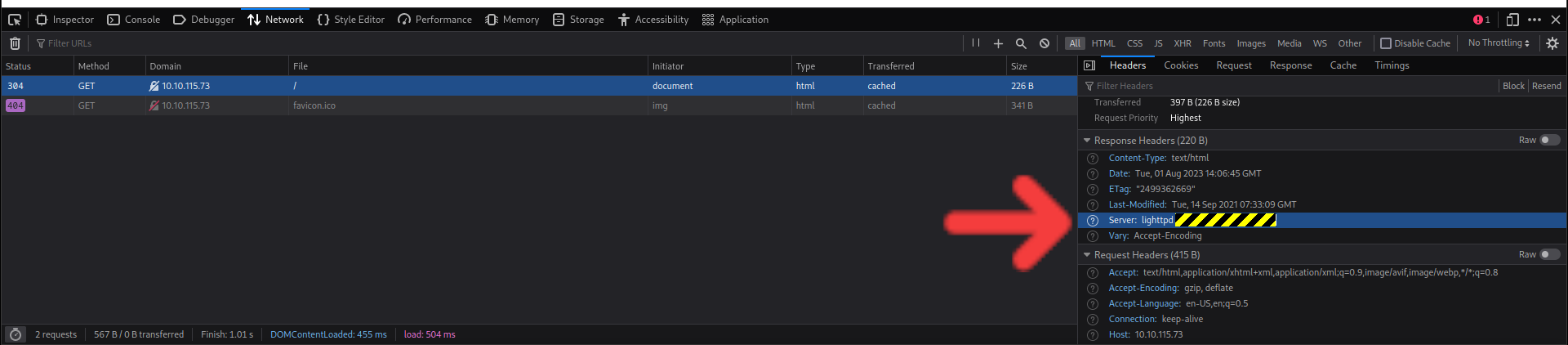
What is the flag hidden in the HTTP server header?
Since my Firefox was opened, I chose Firefox Web DevTools to get the header. However, you could use curl, telnet, or even burp suite to get the flag in the header.
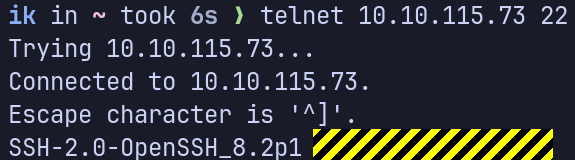
What is the flag hidden in the SSH server header?
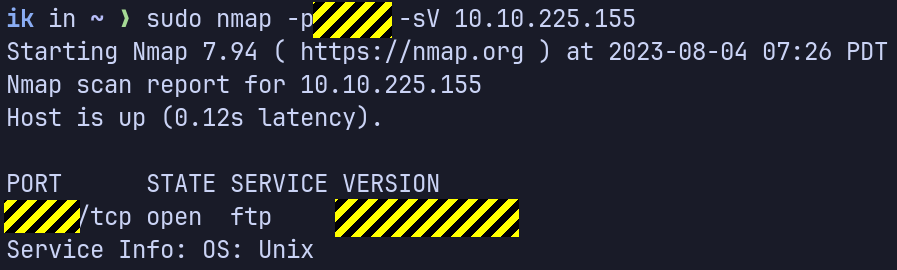
We have an FTP server listening on a nonstandard port. What is the version of the FTP server?
Use -sV flag to find the FTP server version.
-p[ftp port number] |
To only scan the specified port |
-sV |
Version detection |
One line to solve them all
You could solve all the previous questions with one line:
$ sudo nmap -sS -p- -sV -sC [MACHINE_IP]
-sS |
TCP SYN (Stealth) Scan |
-p- |
Scan all ports from port 1 to port 65535 |
-sV |
Enables version detection |
-sC |
Performs a script scan using the default set of scripts |
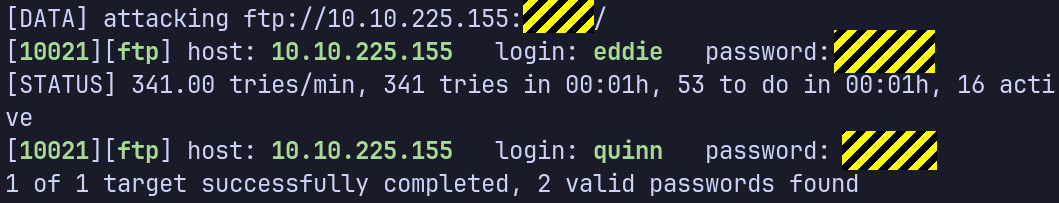
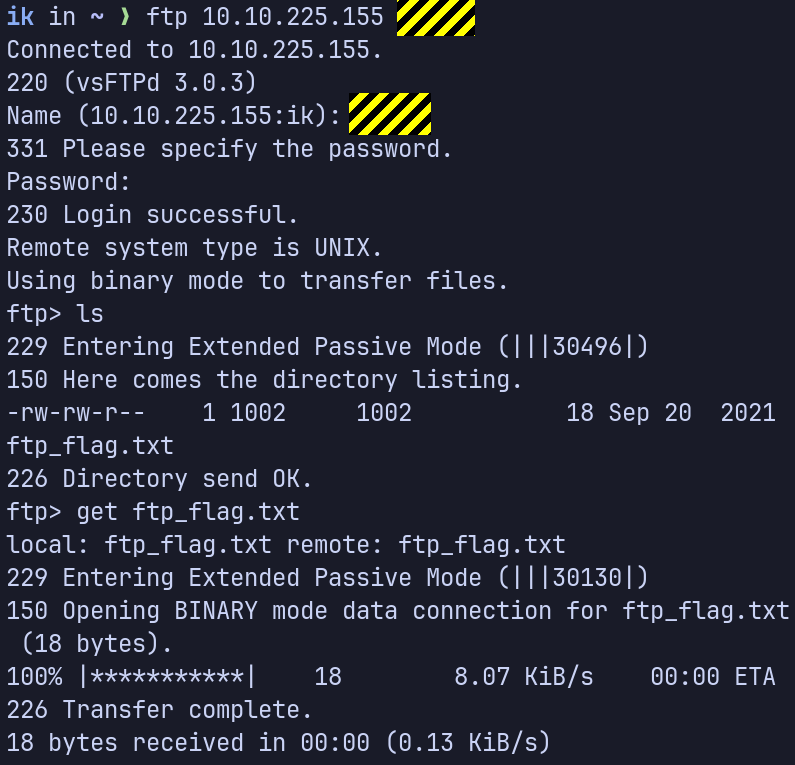
We learned two usernames using social engineering: eddie and quinn. What is the flag hidden in one of these two account files and accessible via FTP?
First, create and write the two usernames, eddie and quinn, on a text file. Then, use hydra to find the passwords for the two usernames. You could use rockyou wordlist, but normally I start with a smaller wordlist, in this case I used the seclists wordlist, 2020-200_most_used_passwords.
$ sudo hydra -L usrs -P /usr/share/wordlists/seclists/Passwords/2020-200_most_used_passwords.txt ftp://[MACHINE_IP]:[ftp port num]
-L |
load several logins form [usrs] file |
-P |
load several passwords from a wordlist |
After hydra find the passwords for the two users, login to FTP and get the flag.
Browsing to http://MACHINE_IP:8080 displays a small challenge that will give you a flag once you solve it. What is the flag?
This is the only question that was challenging and the only one that I enjoyed. It made me re-read the nmap rooms plus Chapter 10. Detecting and Subverting Firewalls and Intrusion Detection Systems. The first thing I thought I should use was the Timing Templates -T. Then, I tried the fragmentation flag -f, the --mtu flag, and a combination of other flags and options, however, none of them succeed. Finally, the only thing that worked was the Null scan -sN.
$ sudo nmap -sN [MACHINE_IP]